Gon Sign ErrSecInternalComponent
Recently, I’ve been using Golang with deanishe/awgo to write Alfred Workflow, which I use a ton.
alfred-pdf2image - Convert PDF to image with Alfred
alfred-devtoys - A Swiss Army knife for developers for Alfred
alfred-paletter - Extract palette from an image
ak - A generator for golang alfred workflow that helps you create boilerplate code.
alfred-opencc - Open Chinese Convert 開放中文轉換
alfred-timelog - You could leverage Alfred and Google Sheets to track your time with ease. The goal is to track your time in a way that is easy to understand how much time you spend on.
alfred-fork-open - Alfred 5 workflow for opening folders in Fork.
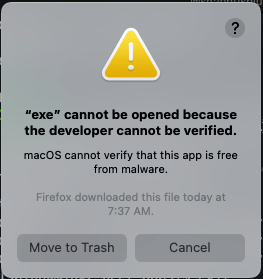
In addtion to use them by myself, I also want to share them with others and publish them to Alfred App Community Forum, which is a website that hosts Alfred workflows forum and allows users to share their workflows with others. When Apple introduced MacOS Catalina, it came with security features to ensure that you only use trusted binary files. This requires that binary files be signed and notarized by Apple itself, otherwise you’ll get an error. This problem is encountered when using the Golang base Alfred Workflow.
Of course, it is possible to allow forced enable in the MacOS “Security and Privacy Preferences”, but this would create a security problem for other users because there is no way to determine if the application being run is trusted. The correct way to do this is to request a “Developer ID Application” certificate and add the certificate to the compile command at compile time。Cause all of my workflows are written in Golang and publish by Github Action. So, this article document the problems I encountered with Gon code sign and how I solved them by following the steps below from Build, notarize, and sign Golang binaries for MacOS with GitHub Actions · KenCochrane.com
Gon
Gon is a tool that allows you to sign and notarize your binaries with a single command and developed by Hashicorp founder Mitchell Hashimoto
Gon Prerequisite: Acquiring a Developer ID Certificate
- Login to Apple Developer and create a new certificate.
- Visit Certificates, Identifiers & Profiles
- Click the + button to add a new certificate and select “Developer ID Application” at Software part and continue to follow the steps to create a new certificate.
- Download
Developer ID Applicationcertificate and double click to install it into your keychain.
Verify that the certificate is installed by running the following command
| |
Gon local code sign
When certificate is ready, we could use Gon to sign the binary file with gon.json configuare file.
gon.json
| |
| |
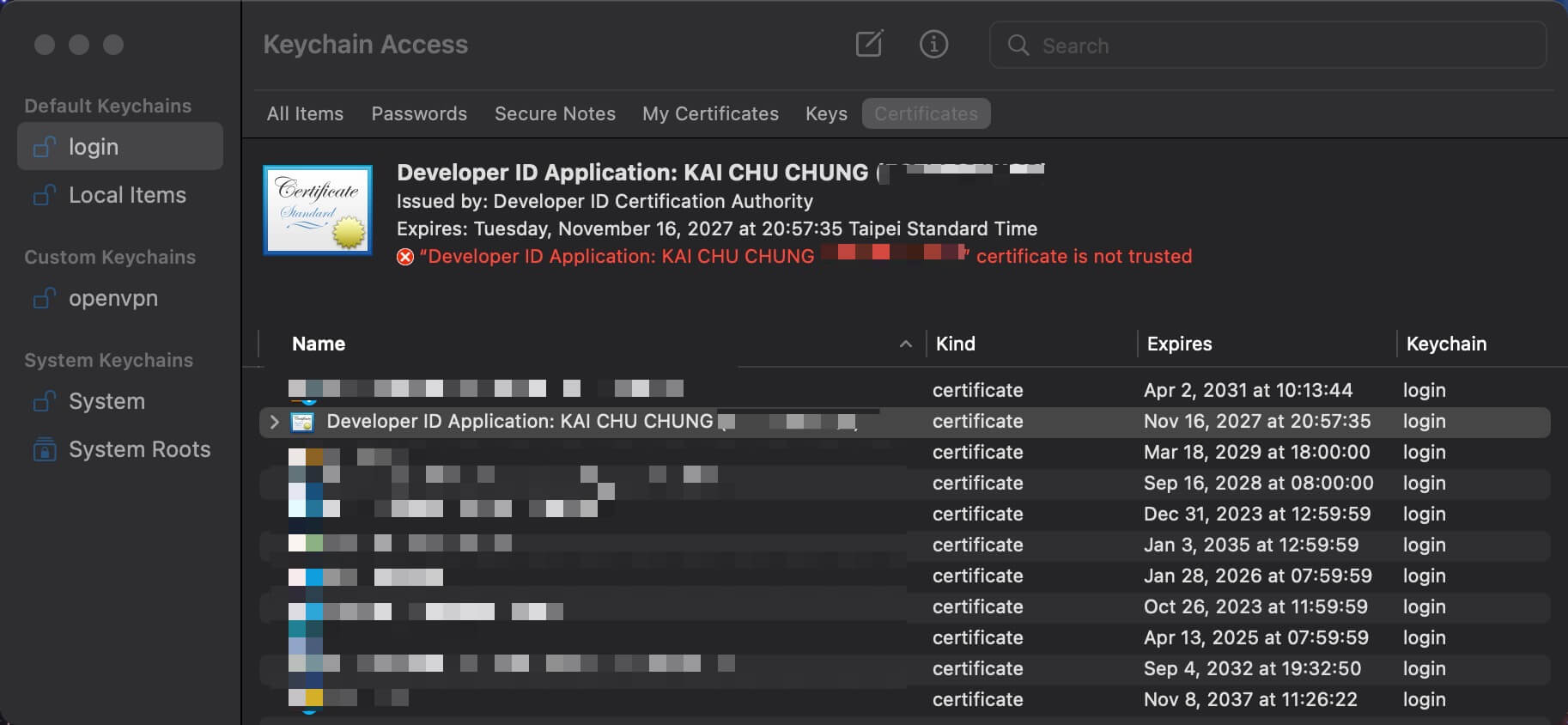
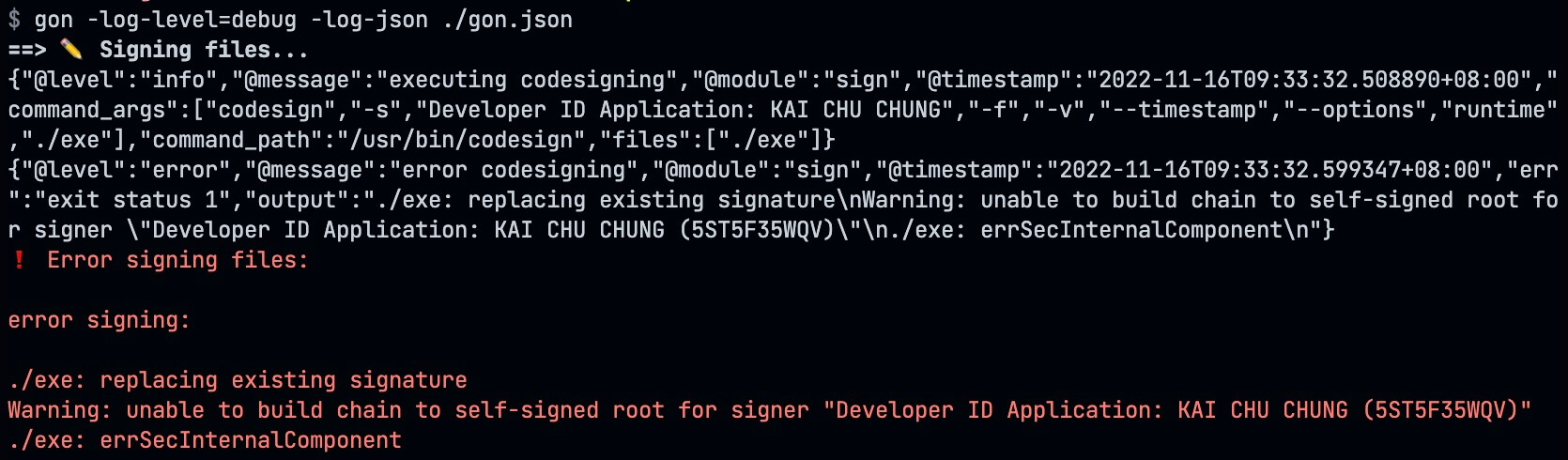
BOOM, we got an error ./exe: errSecInternalComponent when we try to sign the binary file.
Root Cause
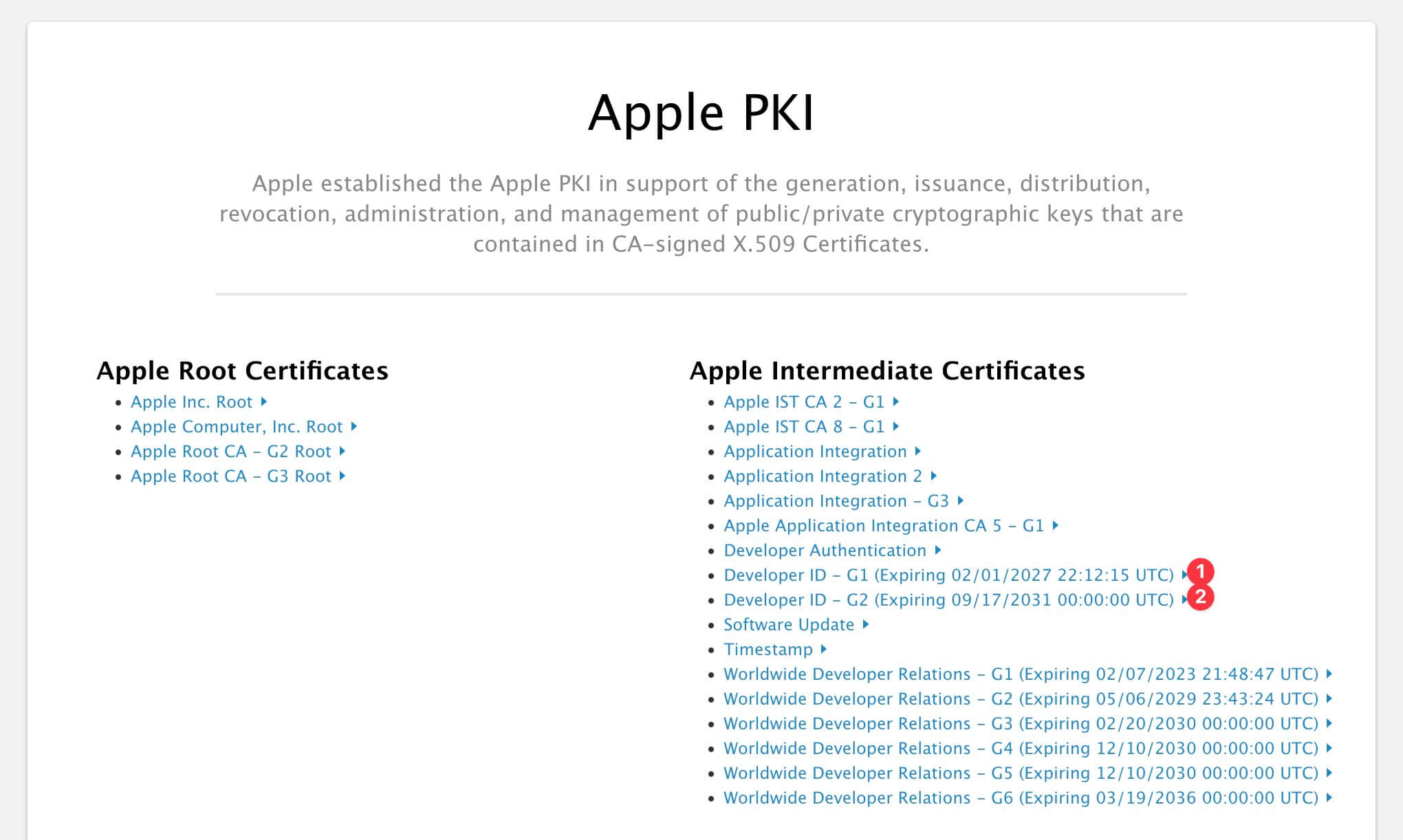
This error is caused by the certificate is not trusted by the system and does not work that even we force enable trust manually in keychain. We could fix this by adding the intermediate certificate to the keychain. We could download the intermediate certificate from Apple PKI - Apple website
There are two intermediate certificates for Developer ID Application certificate, we could download same type as Developer ID Application certificate we request in the beginning and install them into the keychain.
- Developer ID - G1 (Expiring 02/01/2027 22:12:15 UTC)
- Developer ID - G2 (Expiring 09/17/2031 00:00:00 UTC)
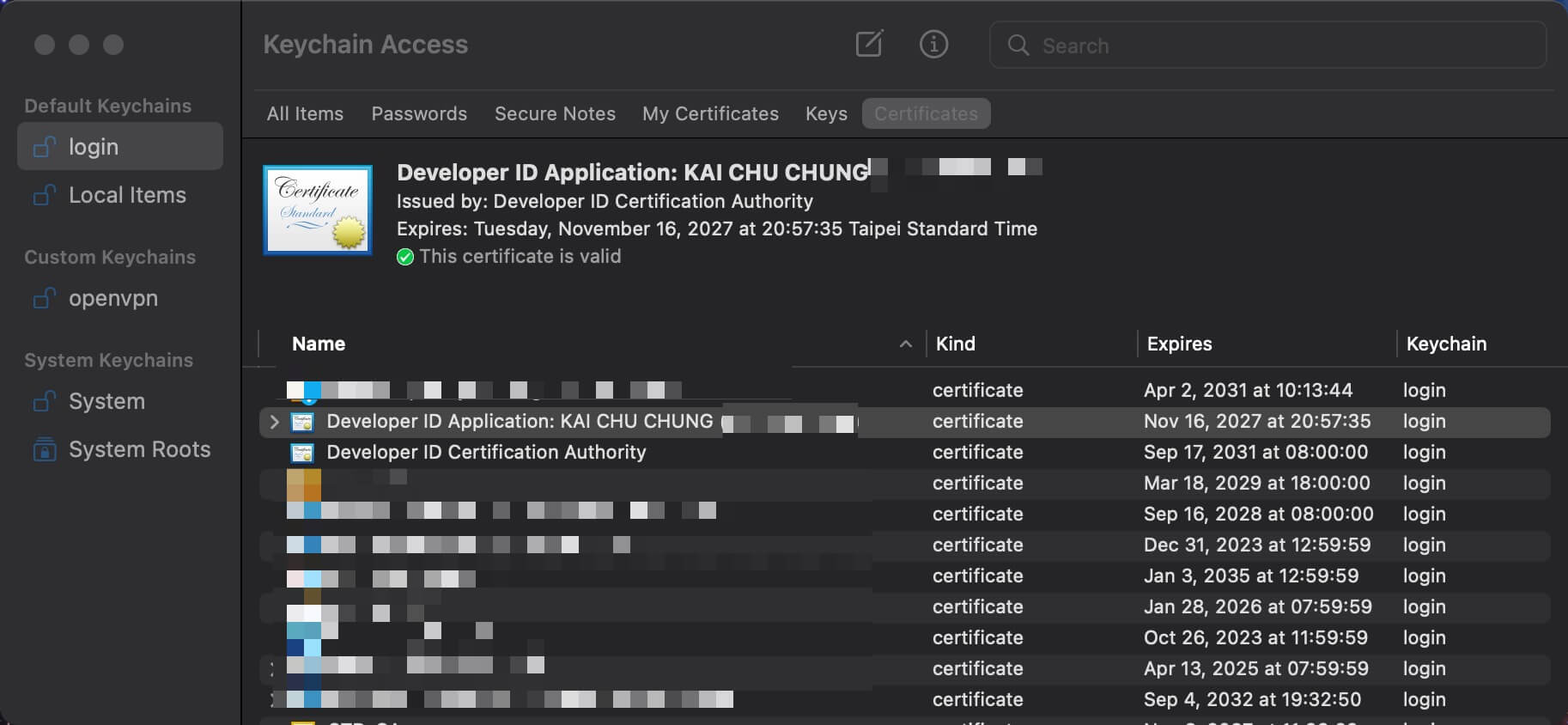
Gon local code sign (success)
Re run the gon command again, we could see the binary file is signed successfully.
| |
Verify the binary file is signed successfully by running the following command
| |
Now, we could use gon to sign and notarize the binary file successfully. The next step is to use gon to sign and notarize the binary file in Github Action relase pipeline.